-
-
Notifications
You must be signed in to change notification settings - Fork 381
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
PB in Firefox causes CSP violation on sites that disallow script-src = self #1793
Comments
|
I believe this is the relevant Firefox bug: https://bugzilla.mozilla.org/show_bug.cgi?id=1267027. |
This comment was marked as resolved.
This comment was marked as resolved.
|
For example on https://web.threema.ch/ (no need to log in, just open the debug console and load the page). |
It's the other way around. It forbids "none" (what the error message is referring to) which is a valid value for src. So you'll actually see the "V8_STACK" error on most CSP sites. |
|
I'm implementing CSP (running it in report-only mode for now) and I got a report like this: I had no clue what was causing it until I found this issue. The report came from a Firefox user-agent. |
|
Firefox bug: https://bugzilla.mozilla.org/show_bug.cgi?id=1267027 The Chrome bug and the uBlock workaround may both be regarding CSPs blocking request redirection to data URIs (rather than CSPs blocking inline scripts created by extensions), but these are related issues. |
|
So, is this a browser bug or is this a PrivacyBadger bug? I'm just trying to enable CSP on my site and encountering this, which means that it must be happening on any page that I've previously visited that had enabled CSP! |
|
Both? Browser bug: extension scripts should not be bound by page CSPs. Privacy Badger bug: can we do something better until browsers fix the problem? (It seems like uBlock did.) |
|
I confirm this.. I ended up here after seeing strange CSP reports about that V8_STACK script.. To recreate this issue:
You will see this: Earlier those 2 violations did not happen. Installing Privacy Badger than caused those to happen. |
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
Privacy Badger version 2018.04.23: - 'sha256-kNsowQfHpWMrbQG7AtSzSuMQg2t/YKwmDWdqeKfm4BI=' - 'sha256-afSIEhWGAPlY458Q4YkhPLVnsVEBh/u5YNlpg6od8TU=' - EFForg/privacybadger#1793 (comment) - https://gitlab.com/kaushalmodi/kaushalmodi.gitlab.io/blob/29fc983ac72fa886ac39bff6b46dc7e426cb993b/netlify.toml#L174-199
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
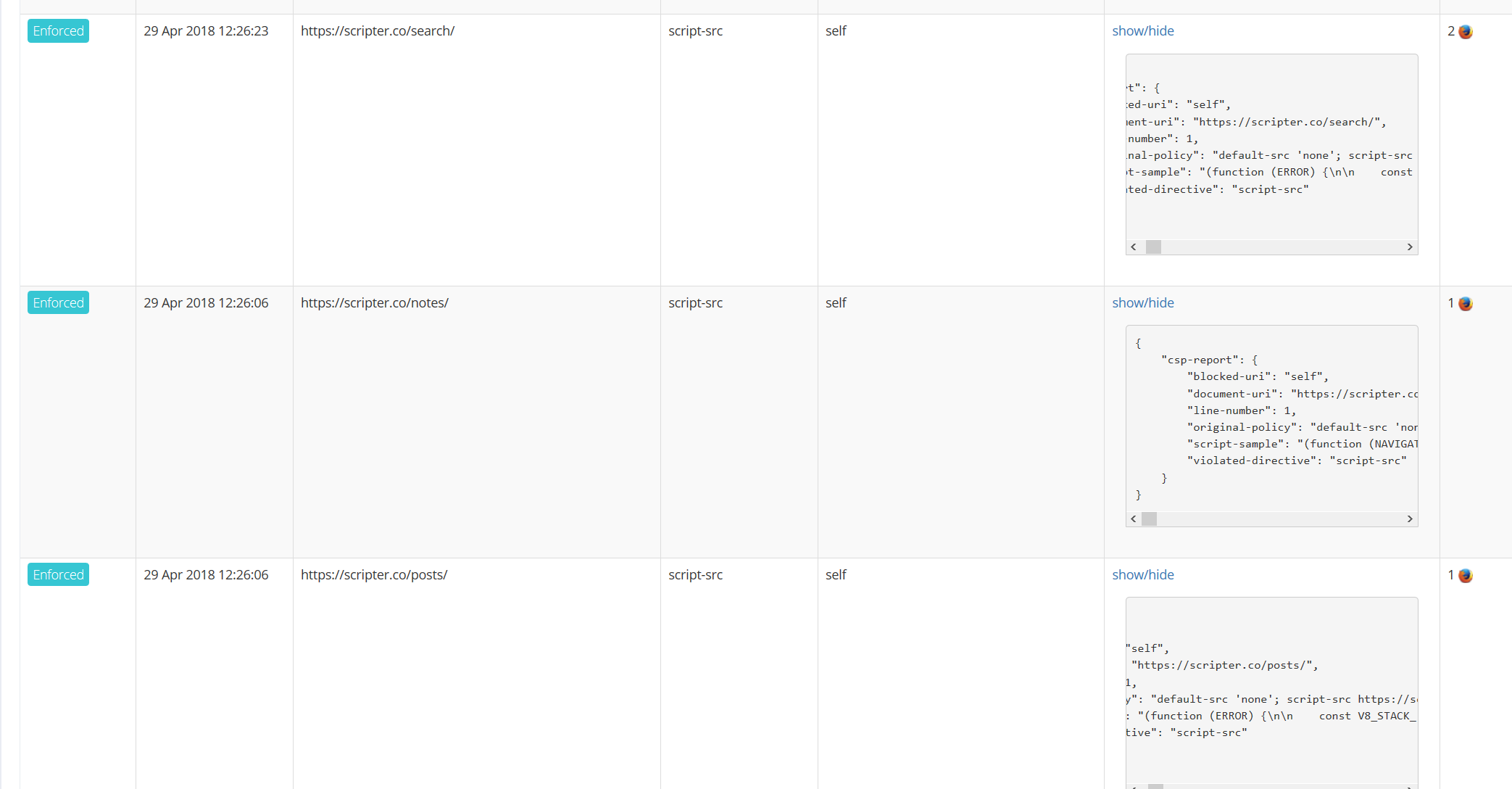
This comes up every time someone visits a site with strict CSP like mine, and has this extension installed. I picked 2 arbitrary sites with strict CSP's to demo this. Open the Web Console in Firefox (Ctrl + Shift +K) and visit https://vincent.bernat.im/en and https://www.josephearl.co.uk/. You will see something like: (That Guess what.. even on this page itself, I get this: So talking about "how often this comes up", the question is more of "how often people care to see the violated CSP's reported for their domain" :) I ended up on this thread because day before yesterday, I started seeing these CSP violations on my CSP reports endpoint (report-uri.com): Now I don't have any of those at least specific to Privacy Badger. I still have other reports on injected scripts by other extensions, which I need to tackle..
This thread is good for now.. until one or more of future updates starts breaking the sha calculated in this thread before Firefox/Chrome do anything about fixing this on their end. If it's not too much trouble, having the hashes in the README would be a good gesture to help people who care about keeping their sites secure using CSP. |
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
|
This might be a Firefox-only issue. Could somebody confirm that CSPs do not apply to extension content script-injected inline scripts in Chrome? |
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
|
I am not able to reproduce on Chrome, but I also wouldn't consider this a bug in Firefox. In this case, Firefox is doing exactly what I am telling it to do by disabling this inline JavaScript. I guess Chrome is able to determine the source of the inline JavaScript (extension vs. website) and automatically add an exception for it since the user has clearly decided to run extensions that they want to interact with websites |
|
It would be awesome if @ScottHelme would weigh on in the best way to resolve this issue. Clearly Privacy Badger is a major cause of CSPs being reported. Is injection into the CSP header a viable option, or is this just going to have to be solved on a per-site basis? Maybe there are other options? |
|
I think Mozilla is making progress on https://bugzilla.mozilla.org/show_bug.cgi?id=1267027 although no idea how close they are to a fix. |
|
I think the best way to solve this is at the browser level. If an extension is doing things to a page then that shouldn't trigger the CSP. Realistically we can't, and shouldn't, expect our CSP to supersede the configuration of the client. If the user has an extension installed that alters styles on the page then those alterations should of course be allowed but the browser should not report on CSP violations that occur as a result. Right now on https://report-uri.com we're constantly adapting our core filter set to remove reports like these so our customers see less noise, but overall it would be better to neutralise this at the source. |
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
This comment has been minimized.
|
We may be able to work around CSP restrictions in Firefox by using Previously: #2497 (comment), #2722 (comment) |

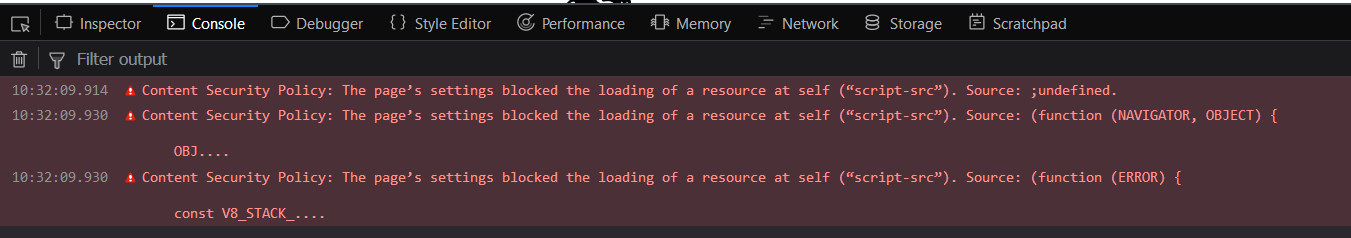

Visiting any site with a Content Security Policy that forbids 'self' scripts results in the following error logged to the console:
Which I believe is fingerprinting.js.
Presumably if a website also has CSP reporting enabled the browser will send a CSP report whenever a Privacy Badger user visits the site, which seems unideal all round.
The text was updated successfully, but these errors were encountered: